Whether it is homes, cars, or videotapes, the trade-off between buying and renting has been thoroughly discussed and analyzed. The right choice for any individual depends a lot on his or her specific situation and industry factors of the moment, such as interest rates, housing costs, and so on.
Enterprise IT also has to continually make similar decisions. Spend capex or opex? Build and depreciate an asset base or rent and return? Exclusive use or shared use? Of course, enterprises have to look professional so they don’t use the consumer-centric term renting. Instead they call it outsourcing.
I am old enough to remember Time BI (before Internet). Anyone less than 60 may not remember this, but there was a time when enterprises bought and built their own WANs in the form of TMUXs that they used to establish a mesh of 1.5Mbps links to connect all their sites to one another. A company called NET was king. Led Zeppelin ruled. Then frame relay came along and allowed enterprises to share WAN infrastructure and reduce costs. Then the Internet came along and chopped the legs out from under frame relay.
The Internet was the world’s first cloud. It is shared, scalable, and cheap. But is it secure? Not so much. However, virtual private networking technology was built to give enterprises secure use of the Internet. Enterprises bought firewall/VPN devices to safely enjoy the economics and flexibility of the cheap rent of the multitenant Internet.
The Internet also had another big advantage – it provided an effective path for enterprises to access applications outside of their corporate environments. SaaS emerged from that. Why buy and support an app yourself when you can just rent a small slice of someone else’s app? Siebel became Salesforce. PeopleSoft became Workday. Exchange became Office365. Pretty much every enterprise is using SaaS for a number of applications that it used to build, integrate, operate, and support itself back in the day.
Then the V word became the IT word when virtualized servers, virtualized storage, virtual desktops, virtual containers, and virtual network function devices arrived on the scene.
That leads me to this anecdote: A physicist, a chemist, and an economist were stranded on a desert island with no implements and a can of food. The physicist and the chemist each devised an ingenious mechanism for getting the can open. The economist merely said: “Assume we have a can opener.”
Virtualization is the assumed can opener. By abstracting the physical reality of infrastructure from the application and users interaction with the services provided by that infrastructure, previous constraints related to ownership, location, underlying resource limitations, and cost are radically reduced.
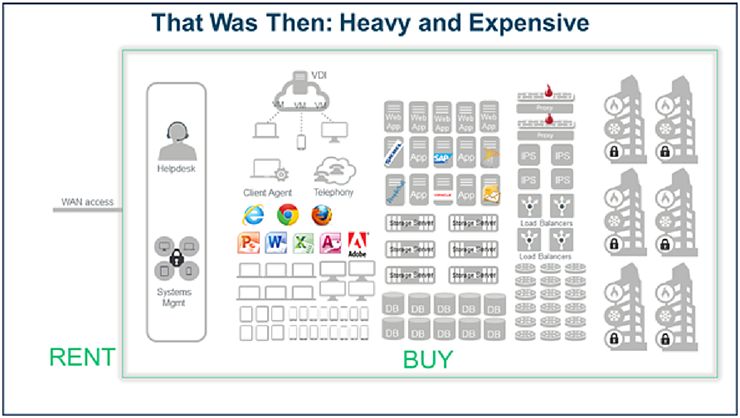
One of the impacts of this is that companies have been able to create a wide range of IT services for enterprises that in the past would have been both too expensive for enterprises to use and not profitable enough for companies to offer. Elastic compute-as-a-service, unbounded storage-as-a-service, DR-as-a-service, API-as-a-service, security monitoring-as-a-service, antivirus-as-a-service, and other service options abound. You can even now get cloud-based wireless network management and cloud-based Layer 2 switches. About all you need to run a small office now is an Internet service contract with someone who provides and maintains an access box with a wireless access point in it, and a few PCs or tablets. I even know a couple of huge multinational companies with multibillion dollar IT budgets that, over the next few years, are looking to collapse their global networks down to a few racks of equipment for their critical databases and, maybe, some PCs or mobile devices for key executives. Everything else will be rented, outsourced, bring-your-own, and do-it-yourself.
Not very many companies I have met with have gotten to the rent everything extreme of the This is Now diagram that appears with this article. Enterprises move slowly. SMBs are moving first. But the agility and economics are too compelling for enterprise not to get there at least partially, and there is no enterprise I have met that isn’t somewhere along the migration path to the This is Now state.
Here are my predictions. I think there are two majorareas in which things are going to evolve rapidly in 2016. In the old enterprise world, internal applications became siloed as workflow and business needs evolved. A lot of effort went into business process management systems to glue applications and data together to meet the needs of the business. As apps move to the cloud, SaaS providers, who are by their nature fairly young, naturally don’t meet the overall needs of the company. So, virtual silos result. What is going to be needed is a complementary form of vBPMS, with virtual data busses, virtual messaging, virtual publish/subscribe, etc., to allow enterprises to glue their rented IT together as well as they did in the past with their bought IT.
As enterprises gain agility and economics by moving to a virtual, extended, rented IT strategy, they are trading off control and security. There will be plenty of security tools that replicate the security controls of the old IT environments, but built for the new virtualized world. But that isn’t going to be enough. Enterprises will need a new tool that embraces every facet of the new rented and virtual IT world to return security and control back to the enterprise.
Software-Defined Perimeter is a new approach to this problem, and it is what my company, Indecium does. This approach overlays both the traditional IT infrastructure and the new to give enterprises complete control over who can connect to what, no matter where the applications are, where the users are, or what device they are using. New solutions addressing the new virtual IT is my prediction as one of the key trends for 2016.