Predatory Malware is Rendering Massive Security Investments Irrelevant
Malware has evolved to evade traditional security defenses and move laterally looking for vulnerabilities. It may even force a generational shift in security.
In a recent CUBE interview with security expert Junaid Islam, host John Furrier asks Junaid a question about the state of security in a new era of nation-sponsored activities and IoT. Both the questions and answers are revealing in terms of what kind of shift in thinking is required for increasingly interconnected enterprises.
“Generational Shift”
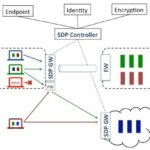
John called it a generational shift. He suggested security might even require a “do over.” What has changed beyond the exponential growth in IoT and digital supply chain connectivity? Perhaps it is the evolution of predatory malware that moves laterally through layers of existing solutions in search of vulnerabilities. Once in it has access to increasingly complex configurations of devices, drivers and servers, a kind of hackers’ playground that was once protected against attack and is now exposed. Because of digitalization the stakes are higher than ever.
As Junaid says, increased interconnectedness leads to increased vulnerability and risk. Yet that is the direction we’re going. Then as nation states get involved and “malware that moves by itself” appears the interconnectedness of the US demands new countermeasures.
These are demands which traditional solutions weren’t architected to address. At conclusion Furrier asks Junaid about efforts to establish a new US national security initiative. Junaid advises that as soon as an approach is taught hackers will evolve to evade them. “We need to rethink how we share information on a worldwide basis.”
Stay tuned…