How to Build a Secure Enclave on AWS

Over the last few years there has been significant security improvements in public clouds. For example, AWS now offers transparent data encryption, key management and secure compute features. Unfortunately, even with the advances in public cloud computing, organizations like financial institutions have been unable to leverage these services because many analysts work in secure facilities that have no Internet access.
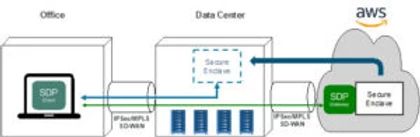
Secure Enclaves perform like an internal data center application from a performance and connectivity aspect. Conceptually Secure Enclaves provide a new compute model in which the “cloud is migrating inside the regulated data center” versus the existing “migrating to the cloud” design.
-
-
A Secure Enclave has many interesting security attributes that differentiate from existing hybrid public-private cloud designs. First, one of primary barriers that regulated entities have when utilizing public cloud is that access to cloud resources is not allowed due to the risk of unauthorized data access.
•The Secure Enclave ensures only users at facilities controlled by the enterprise who also have valid data center access can access protected applications.
Second, a new generation of laterally moving malware which is able to destroy or steal data by pivoting thru the authorized user’s device needs to be blocked.
•Indecium’s solution utilizes a Software Defined Perimeter (SDP) application layer connection model that blocks laterally moving malware.Our solution allows the strict partitioning and role based access that is a standard feature of regulated data centers to be re-created in public cloud environments
For entities like financial and government agencies the Secure Enclave is a significant breakthrough as it allows them to benefit from the agility and cost benefits of the AWS commercial marketplace.
Stay tuned as we share our lessons learned addressing challenges with confidentiality and the cloud by signing up for our updates.
-


