Winning A Battle Yet Losing The War
Security spending is up yet but so are cyber attacks – what’s wrong with this picture?
Gartner is forecasting that a record setting $100 Billion will be spent on security in 2016 but no one is predicting a decline in cyber attacks. The crux of the problem is that bulk of security spend is on point products that meet specific compliance requirements – not stopping cyber attacks. This is critical failure in cyber strategy confuses even some security professionals.
Security point products are like chess pieces on a board. Buying better security product is like upgrading to a Knight from a Pawn – that sounds good on the surface. Unfortunately, cyber attackers look at the whole board and can avoid individual security controls. Or worse, cyber attackers often incorporate a security control into their kill chain just as a Chess Master trick opponents to expose their King.
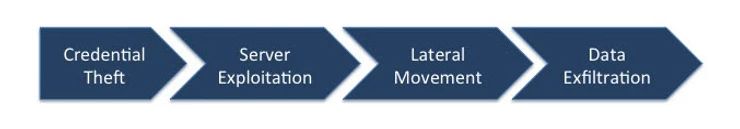
Cyber Kill Chain
To understand the current dilemma let’s look two examples.
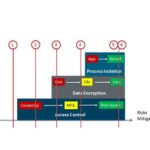
Most Fortune 500s deploy Data Loss Prevention (DLP) solutions to stop confidential data from being emailed or uploaded. Unfortunately, cyber attackers steal the credentials of authorized users to access encrypted data stores and then encrypt ex-filtrated data – avoiding DLP systems completely.
While DLP solutions are not useful in stopping data theft at least they are not a part of the cyber kill chain – that title goes to the remote access VPN. This compliance bedrock was utilized in so many cyber attacks (OPM, Sony, Target etc) that you’d think people would be throwing them out the window.
VPNs allow remote devices to integrate to Kerberos ticketing systems, auto-update services, and management systems – so are critical to ensuring corporate devices follow compliance guidelines.
Unfortunately, when the VPN credential is stolen or the remote VPN device is compromised the cyber attacker is free to move around the network and utilize any protocol they wish to exploit servers and steal data. Thus VPNs have become a de facto part of the cyber kill chain.
If you really wanted to reduce cyber attacks you must focus on the kill chain. At minimum you must stop VPN credential theft, ensure data is only decrypted on the device of the entitled user, block lateral movement and have some mechanism to spot device tampering. Without these steps the cyber risk equation does not change (no matter how well you meet compliance standards).