Defending Against the APT Paradigm
A new paradigm is needed in the industry. The concept of networking was created with the logic that connectivity is enabling and this concept was implemented in such a way where security was simply an afterthought and has created a situation where security is always in catch-up mode.
In those attacks which are not classified as APT, this is normally not very difficult. However in the case of APT, it is very difficult to profile an attack and get an idea on which technologies would have helped or mitigated the attacks. It’s often impossible to track down the initial point of compromise in an APT attack because they tend to cover their tracks very well.
Taking into account the technology that’s in use today, it’s very challenging, if not impossible, to create a defensive security system which would mitigate an APT attack.
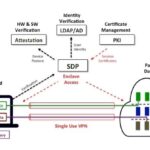
The reality of advanced, state-sponsored attacks are that if they want to get into the network – they will. As a result the best thing an organization can do is segment their applications, install early warning detection system, and respond to incidents in a proper manner.
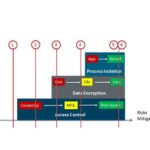
The problem is that most networks today are still relatively “flat”- meaning that both authorized and unauthorized users are able to access sensitive servers on the network. This allows for malware and lateral movement attacks to spread across the entire organization, making it very hard to remediate.
The challenge with mitigating APT attacks comes down to the sophistication of the particular attack. First consider that APT attacks are commonly executed using zero-day exploits, exploits that the developer does not know exist, and with newly generated malware which does not get detected by today’s signature-based security products. This means that it’s very difficult to rely on existing security controls to prevent and detect the exploit or malware.
Another good methodology for detecting these attacks is to place honeypots (or honeynets) on the network near the applications that are being protected. This will provide the organization with an early warning system when an attacker starts to scan your network or probe servers. It also produces very few false positives since nobody should be accessing the honeypot for any legitimate reason. These segmentation strategies and detection systems are key to both preventing and containing APT attacks.
Recently, one client called us in because they had discovered that an attacker was pivoting throughout their network and created intrusion detection alerts. As it turns out, the attacker had been inside the network for more than two months before actually triggering any of the internal security systems.
In terms of the top mistakes that companies often make which allows intruders in:
Lack of User Awareness – User awareness training is critical these days. The most common point of entry into networks is through human error – phishing, USB sticks, etc.
Lack of Resources – It’s very common for large organizations to have a limited set of resources for security. Security is one of the most challenging problems in business that exists today and it requires a significant amount of resources as a result.