Ransomware Threats are on the rise – What can you do?
In reviewing research from many companies, the level of threats to enterprise organizations is on the rise.
The number of bad actors, attackers, insider threats and much more has been plaguing businesses for multiple years. Over the past year to eighteen months, Ransomware attackers has become much more aggressive and lethal. Ever since the beginning of this trend in 2006 with the first discovery of ransomware in Russia, the security industry has been on the ropes.
For years, targeted ransomware has been one of the main cyber risks for businesses and other large organizations. However, the past twelve months have seen ransomware attackers become more aggressive, finding more ways to increase the reach of their attacks, and becoming more ambitious by mounting a number of audacious and highly disruptive attacks.
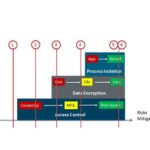
The identification of these threats is no longer a “nice to have”. Identification of threats as early as possible in the kill chain is critical to the success of the battle against ransomware as well as any other outsider or even insider threats. When you look at the MITRE ATT&CK framework, the tactics and techniques of Reconnaissance, Initial Access, Privilege Escalation, Credential Access and Lateral Movement are the phases that should alarm you enough to take immediate action. Noticing these anomalies, user behavior patterns, and unusual actions taken in your network can be the early warning signs you need to stop a Ransomware attack before execution and lockdown.
A Graph database will give you the ability to use the connected data from all of your disparate tools and data sources to quickly identify threats and further your SOC teams threat hunting practices.
The attack against Colonial Pipeline in the U.S. in May 2021 caused significant disruption and prompted concerns about the nation’s fuel supplies. In the same month, an attack on Ireland’s national health service, the Health Service Executive, forced it to cancel thousands of appointments and initiate a recovery operation that took a very long time to conclude.
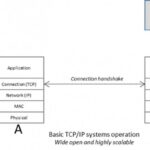
Everyone is aware that the lack of visibility because of these disparate tools, that don’t share alert and event data, brings about significant alert fatigue for all of your security analysts. Your SOC and or NOC analysts are in need of a solution that provides what they have needed for years. A system that can bring all of the data together with automated deep link analytics, algorithms that allow for customization of queries for finding commonalities and relationships using in database machine learning and most of all, providing the correlation of events that will enable the reduction of false positives and false negatives.
The number of targeted ransomware attacks is much higher once you figure in all of the unconfirmed and unreported attacks. Confirmed attacks from known targeted ransomware families are a sample of the overall number of attacks. You also have to consider that many targeted ransomware attacks are halted before payload deployment with proper alerting, this in turn causes the attack to not be associated as ransomware. When you consider that most targeted ransomware operators recompile their ransomware for every new attack, this means that variants exist in multiple versions of each kind of ransomware. Because of this fact, the variant of the ransomware used in an attack may be blocked by generic or machine learning-generated detections rather than a detection linked to that ransomware family. This will skew the number of attacks being identified.
Graph offers in database machine learning that will enable you to quickly identify and potentially stop these attacks before the payload is deployed or potentially after deployment but before it is executed. In the majority of attacks, the bad actors do not immediately execute the attack, they drop the payload and allow it to be ingested in daily and weekly backups ensuring a more robust attack once it is executed.
Identification is the key
Identifying an attack before payload deployment or potentially after deployment and before execution is the critical mass that organizations must achieve. Even with the government and law enforcement crack down on ransomware gangs over the past few years, the threat actors remain undeterred and the cost of these attacks are on the rise. The rise of fees or ransom paid is not as much as the cost of mitigation and cleanup.
If you are able to identify a threat through connected data visibility with a graph database, then your chances of reducing that cost of mitigation and preventing the need to pay the ransom becomes much more realistic.